
Useful tools for analysts…
Phishing & Malware
-

PhishTool
PhishTool gives human analysts the power to reverse engineer phishing emails, to better defend against them. PhishTool is to phishing emails as a disassembler is to malware or a forensic toolkit is to file systems.
-

Talos Intelligence
IP & Domain Reputation Center. The Talos IP and Domain Reputation Center is the world's most comprehensive real-time threat detection network. Search by IP, domain, or network owner for real-time threat data.
-

Email Header Analyser
Official Microsoft tool to simplify email headers and parse the header information into easier to read text, ultimately helping analysts identify spoofed emails.
-

abuse.ch
Databases containing IOCs of malicious URLs, malware samples, botnets, malware distribution sites and more. Use this to query your findings for any existing malicious IOCs.
-

Shodan.io
Shodan is the world's first search engine for Internet-connected devices. Use Shodan to discover everything from power plants, mobile phones, refrigerators and Minecraft servers.
-

yarGen
yarGen is a generator for YARA rules . The main principle is the creation of yara rules from strings found in malware files while removing all strings that also appear in goodware files.
-

IPinfo.io
With IPinfo, you can pinpoint locations, find an IPs hosting provider and ASN, and more details to query an IP address.
-

ANY.RUN
ANY.RUN is a malware sandbox that allows you to see real-time results of processes and connections a malicious file makes. Also useful for phishing links.
-

vx-underground
A great site to download malware samples, read Windows and Linux papers and view the APT collection.
-

ATT&CK Framework
A knowledge base of adversary tactics and techniques based on real-world observations. The ATT&CK knowledge base is used as a foundation for the development of specific threat models and methodologies.
-

AlienVault - OTX
AlientVault - Open Threat Exchange is a Threat Intelligence platform supported by the security community who contribute, discuss, research, validate and share threat data.
-

VALHALLA YARA
A collection of the newest YARA rules provided by Nextron Systems (by Florian Roth). See more from Nextron Systems like Sigma and LOKI rules.
Miscellaneous
-

Uncoder.IO
Uncoder.IO is the online Sigma translation engine for SIEM saved searches, filters, queries, API requests, which helps SOC Analysts, Threat Hunters, and Detection Engineers to translate detections on the fly.
-

CyberChef
A simple, intuitive web app for analysing and decoding data without having to deal with complex tools or programming languages. CyberChef encourages both technical and non-technical people to explore data formats, encryption and compression.
-

SafeLinks Decoder
This tool allows you to take a Microsoft SafeLink and decode it back to its original URL. Saves you the time and hassle when trying to identify the true destination of a link.
-

DorkSearch
DorkSearch is a tool that gives you a list of prebuilt templates for Google Dorks for different use cases. From exposed admin logins, gov sites to webcam portals etc.
-

LOLBAS Project
The LOLBAS project aims to document every binary, script, and library that can be used for Living Off The Land techniques.
-

GTFOBins
GTFOBins is a curated list of Unix binaries that can be used to bypass local security restrictions in misconfigured systems.
-

Javascript UnPacker
Unpacks Javascript that had its vars and arguments renamed to make it harder to debug and ultimately harder to deobfuscate by just reading.
-
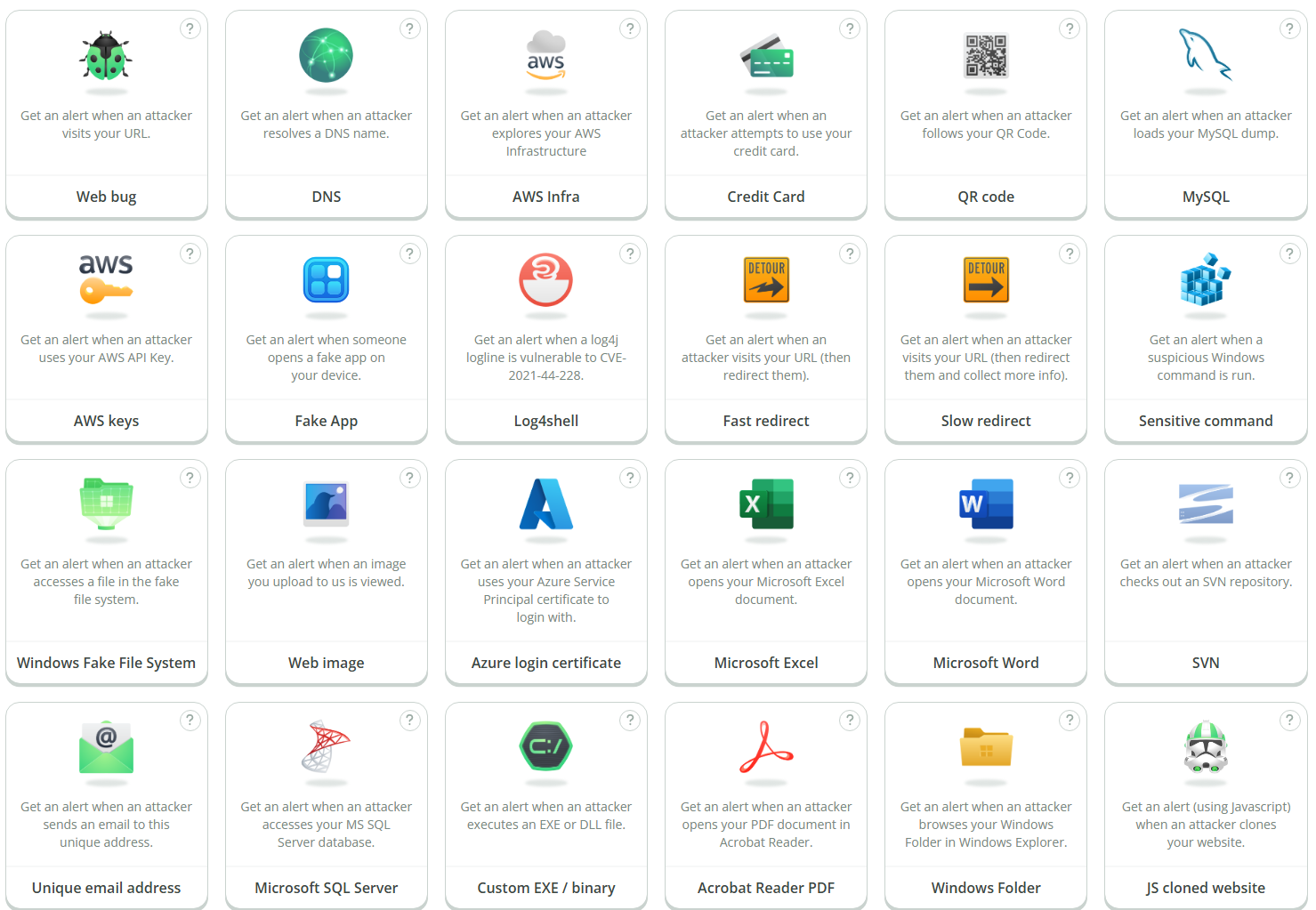
Canarytoken
Canarytokens are like motion sensors for your networks, computers and clouds. You can put them in folders, on network devices and on your phones. Place them where nobody should be poking around and get a clear alarm if they are accessed.
-

SIFT Workstation
The SIFT Workstation is a collection of free and open-source incident response and forensic tools designed to perform detailed digital forensic examinations in a variety of settings.

