Phishing: Fake Microsoft Login Page
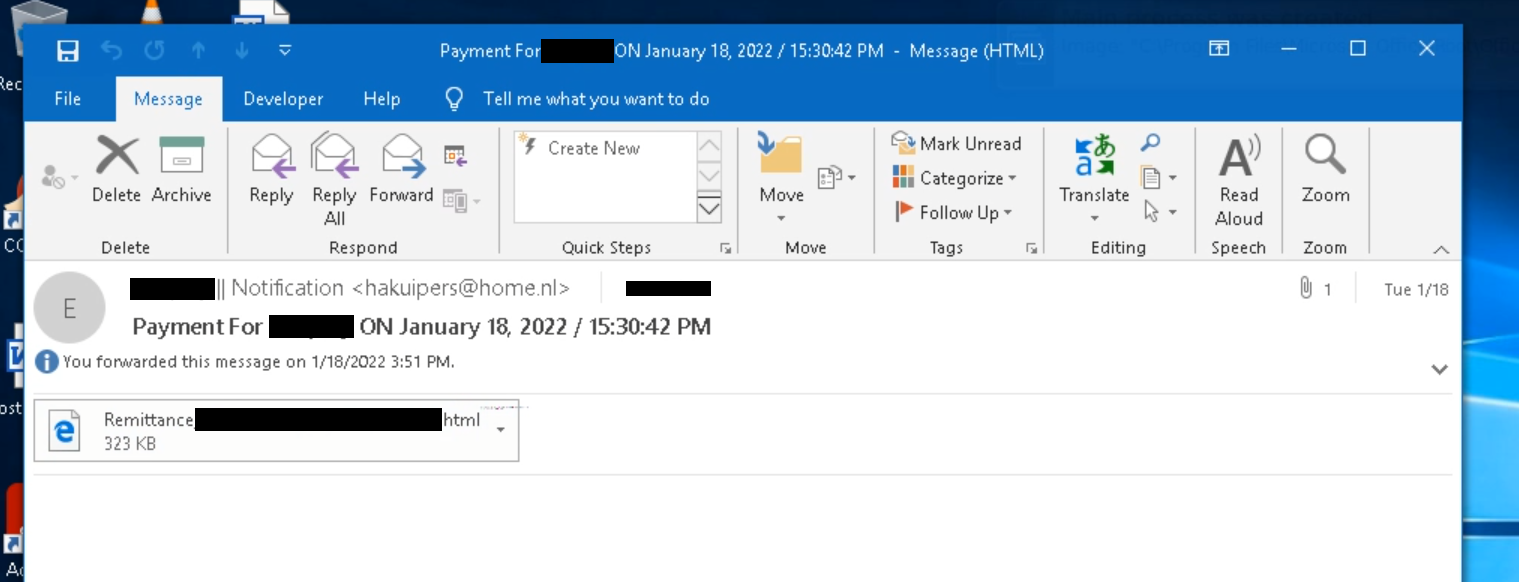
An HTML file containing obfuscated Javascript was sent via a spear phishing email campaign lately. Although the phish isn’t the most sophisticated out there, it did manage to get past our email filtering and was only detected by EDR shortly after through a post-exploitation alert.
HTML styling and jQuery were used to mimic the sign-in page for Microsoft. But, being an HTML attachment, it couldn’t even get past some of the most computer illiterate users in our company, and thankfully no downloads were detected through alerts and manual investigation…*sigh of relief*.
For the file itself, it contains a substantial amount of obfuscated JS/HTML code with URL escape codes present throughout. Being very easy to unravel, the first few lines of code were revealed, with clear indicators that this is a credential phishing campaign.
After viewing the rest of the code briefly in Sublime Text, it was obvious to me (even for someone with very little coding knowledge as of this write-up) how this credential phish works.
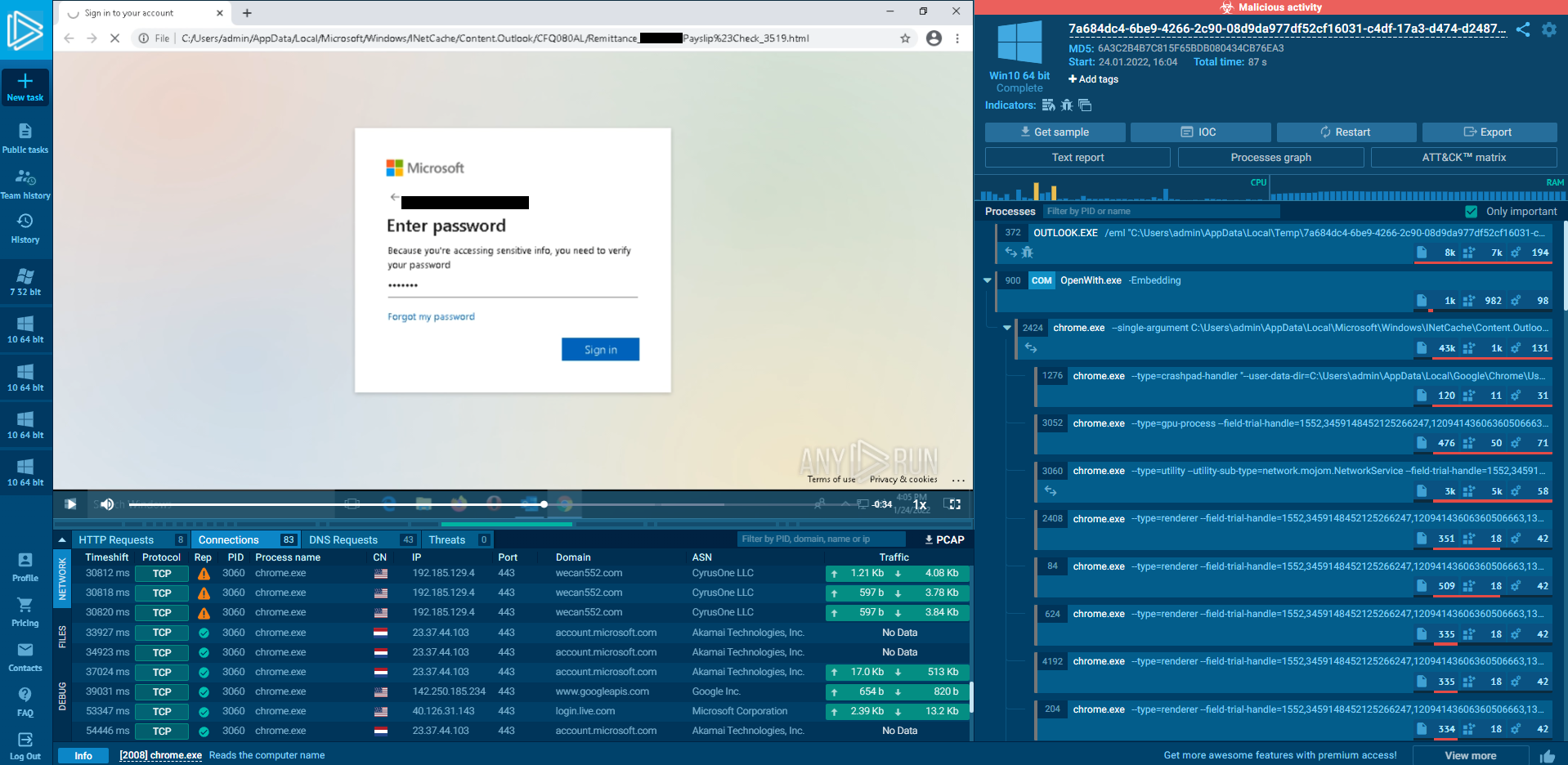
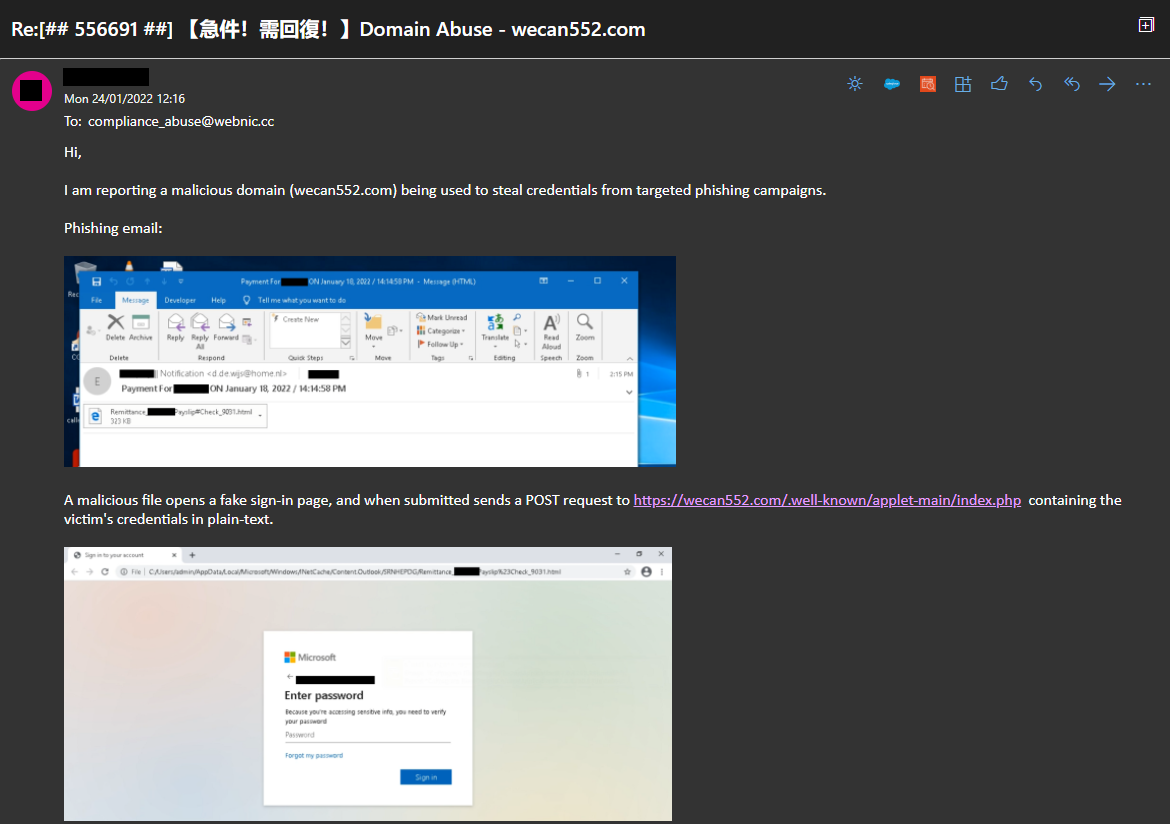
Once the victim submits their password in the input field, it sends the form-data (in this case the plain-text password) as a POST request to an ‘index.php’ file hosted on wecan552[.]com.
Scrolling throughout the code, I also noticed a few imports of official Microsoft branding images in .svg format. These were used to make the sign-in page even more believable.
Even with this targeting around 50-100 employees, I noticed the code was directly quoting only one email address per attachment. It looks as if the threat actor is manually spear phishing rather than using an automated process to determine email addresses based on who clicked the link. But I guess that’s one of the disadvantages to using a local HTML file rather than directing a victim to a landing page online.
RUNNING THE PHISH IN ANY.RUN
After analysing the code and understanding how it functions, it was time to run the phish in a sandbox environment and see what other connections are made if any at all. I opened the HTML file in ANY.RUN and entered a random string into the field and submitted the POST request. In the connections tab, it only made a TCP connection to - ‘//wecan552[.]com/.well-known/applet-main/index.php’. Other than that, no other malicious activity was seen, no pull requests or malware was downloaded. This was a simple phish for credentials.
The domain provider for wecan552[.]com was ‘webnic[.]cc’.
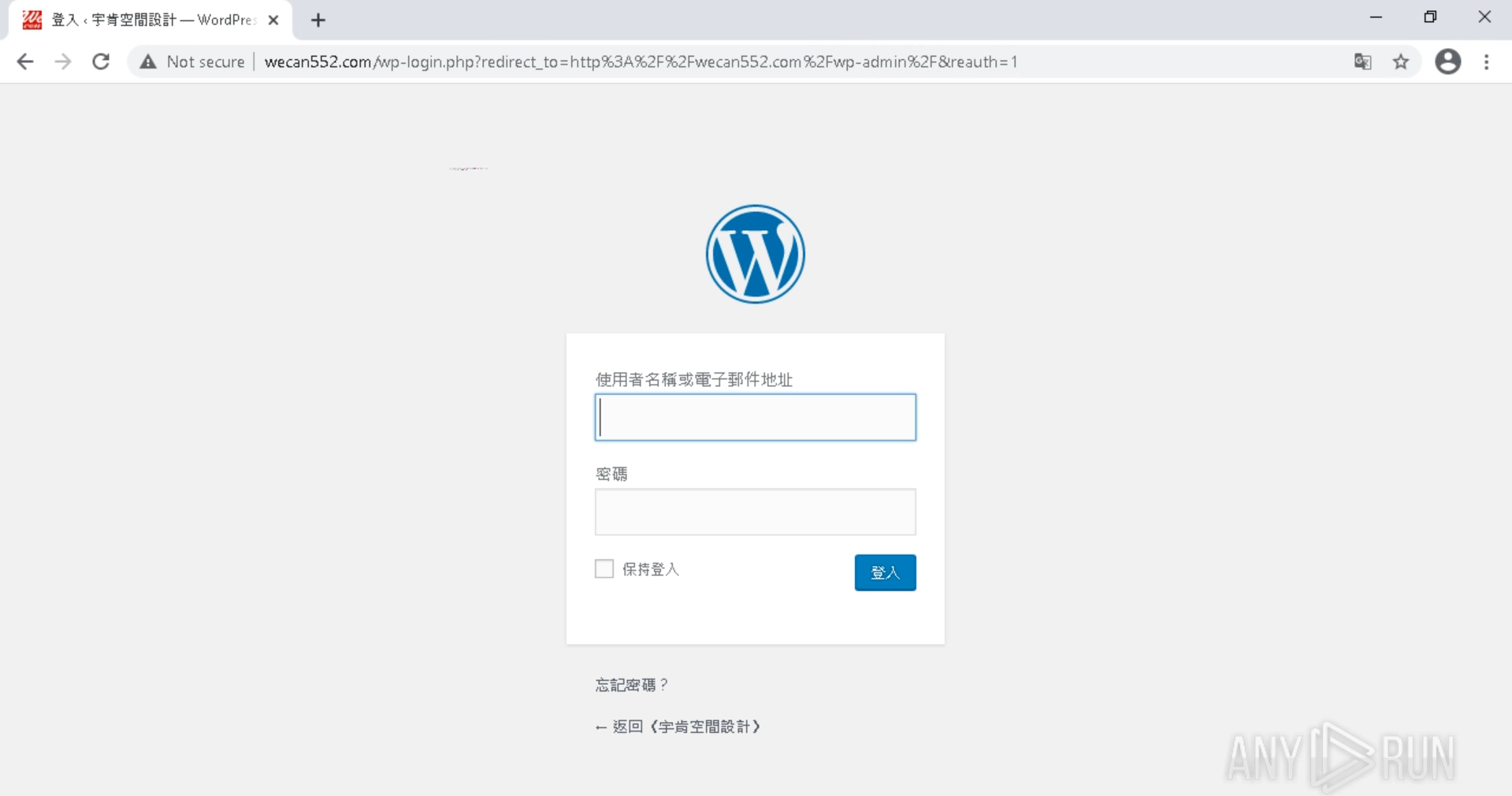
Over the 3-4 days I was monitoring this domain, it shifted between displaying nothing (blank web pages) to disguising itself as an interior design company located in Taiwan.
When I noticed the interior design front, HTTP requests were made to several URLs where the images/videos were being hosted. From the URL connections in ANY.RUN, I found out this was a WordPress site. So I decided to poke around to see what else I could find, so I checked for the default admin login page by going to ‘wecan552[.]com/wp-admin’.
Translating the web page I could see what the domain may have previously hosted - “Yuken Space Design”. This could have been a previous front for the phishing threat actors but my Googling couldn’t find any details on Yuken Space Design so I decided to leave it at that and not step into a gray area with the admin page.
At this point, there was no reason to dig any deeper other than personal curiosity. I had more than enough information to act on and block the IPs and URLs as well as create a threat hunting query in Defender 365 to be used as a detection rule.
As a defender, I should get into the habit right away of reporting malicious domains to their providers to get them taken down as it helps other defenders and businesses from being impacted by similar phishing or malware attacks. So I contacted the domain providers and provided sufficient evidence to warrant a takedown.
And within the next day, the site was no longer reachable…
Note: This was my first attempt at doing a write-up of a spear phishing campaign. I know this isn’t the most sophisticated phishing campaign out there, but I did learn a few things when investigating and trying to connect the dots, instead of solely relying on automated alerts and virus scans…